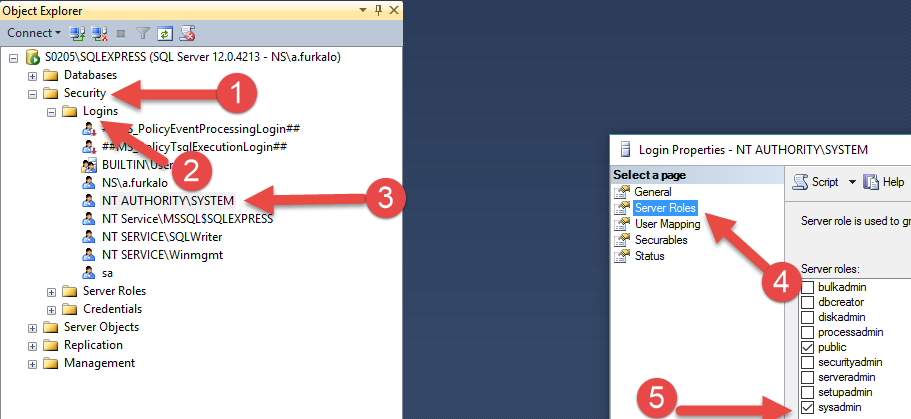
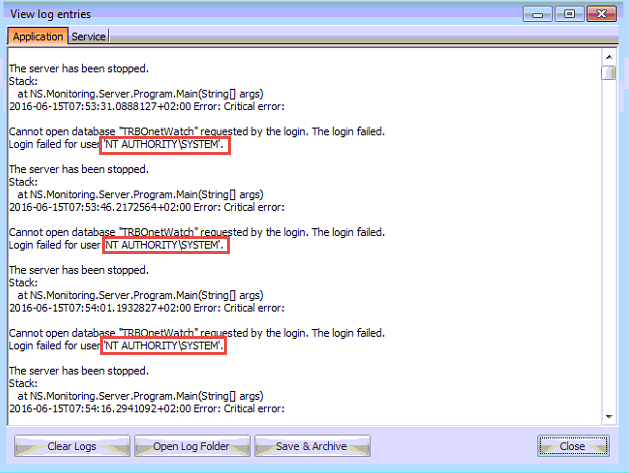
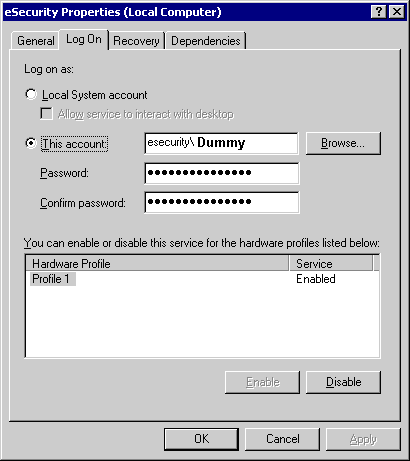
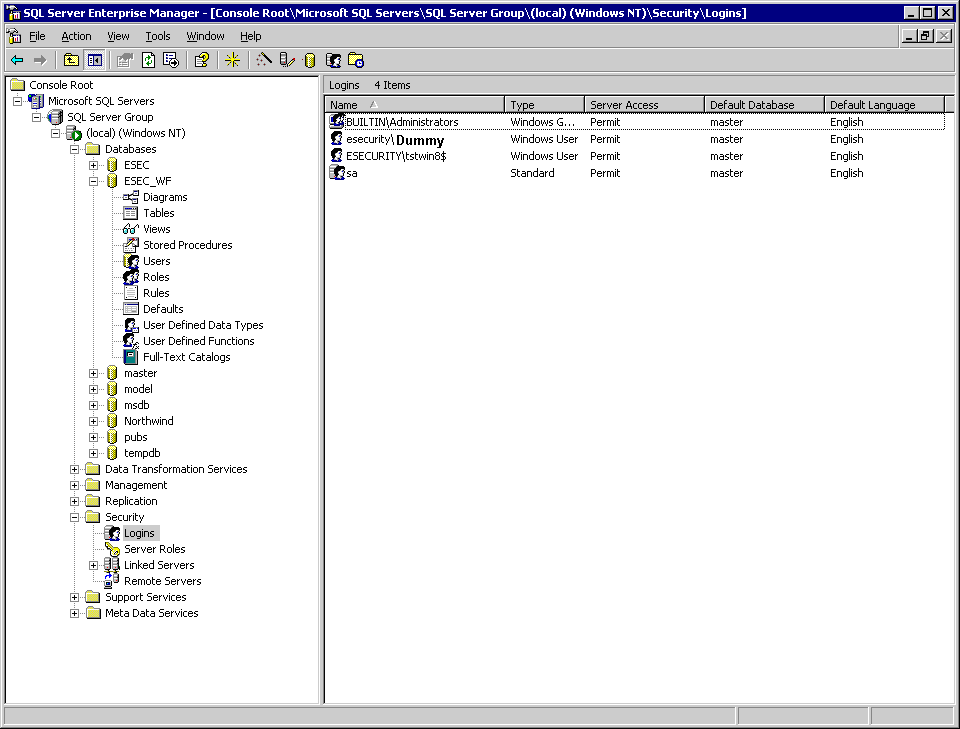
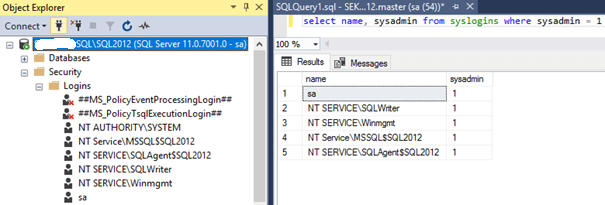
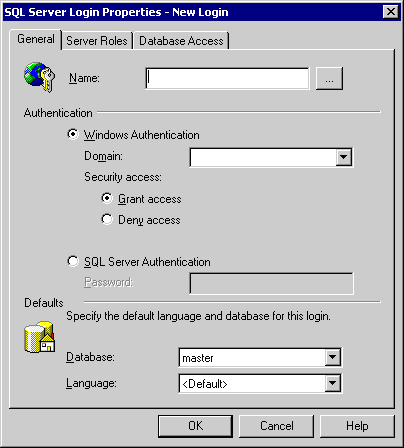
SQL SERVER - FIX : ERROR : Cannot open database requested by the login. The login failed. Login failed
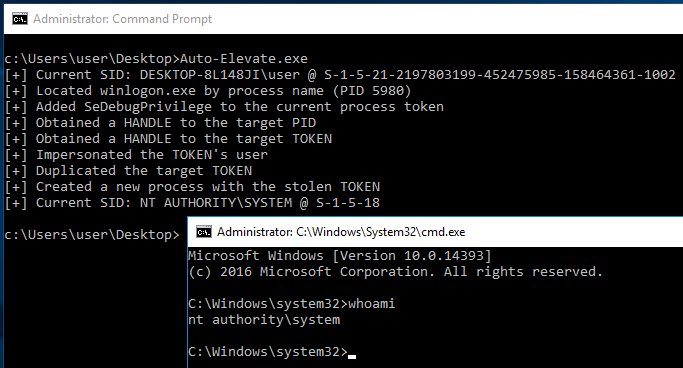
GitHub - FULLSHADE/Auto-Elevate: Escalate from a low-integrity Administrator account to NT AUTHORITY\SYSTEM without an LPE exploit by combining a COM UAC bypass and Token Impersonation
![DBMS-MSSQL:11006#916] The server principal “NT AUTHORITY\SYSTEM” is not able to access the database under the current security context | SQLBackupAndFTP's blog DBMS-MSSQL:11006#916] The server principal “NT AUTHORITY\SYSTEM” is not able to access the database under the current security context | SQLBackupAndFTP's blog](https://sqlbackupandftp.com/blog/wp-content/uploads/2018/06/Map-User-to-Database-step-1.png)
DBMS-MSSQL:11006#916] The server principal “NT AUTHORITY\SYSTEM” is not able to access the database under the current security context | SQLBackupAndFTP's blog

mpgn on X: "From nt authority\local (or network) service to nt authority\ system ⚔️ 1⃣ Shell as nt authority\local service / network 2⃣ Run FullPower from @itm4n ✓ Getting SeImpersonatePrivilege to enabled 3⃣

Unable to revoke permissions for 'NT AUTHORITY\SYSTEM' on SQL Server 2016 - Database Administrators Stack Exchange

Event Log Error: NT AUTHORITY\SYSTEM is not setup for single sign-on - ERP 10 - Epicor User Help Forum