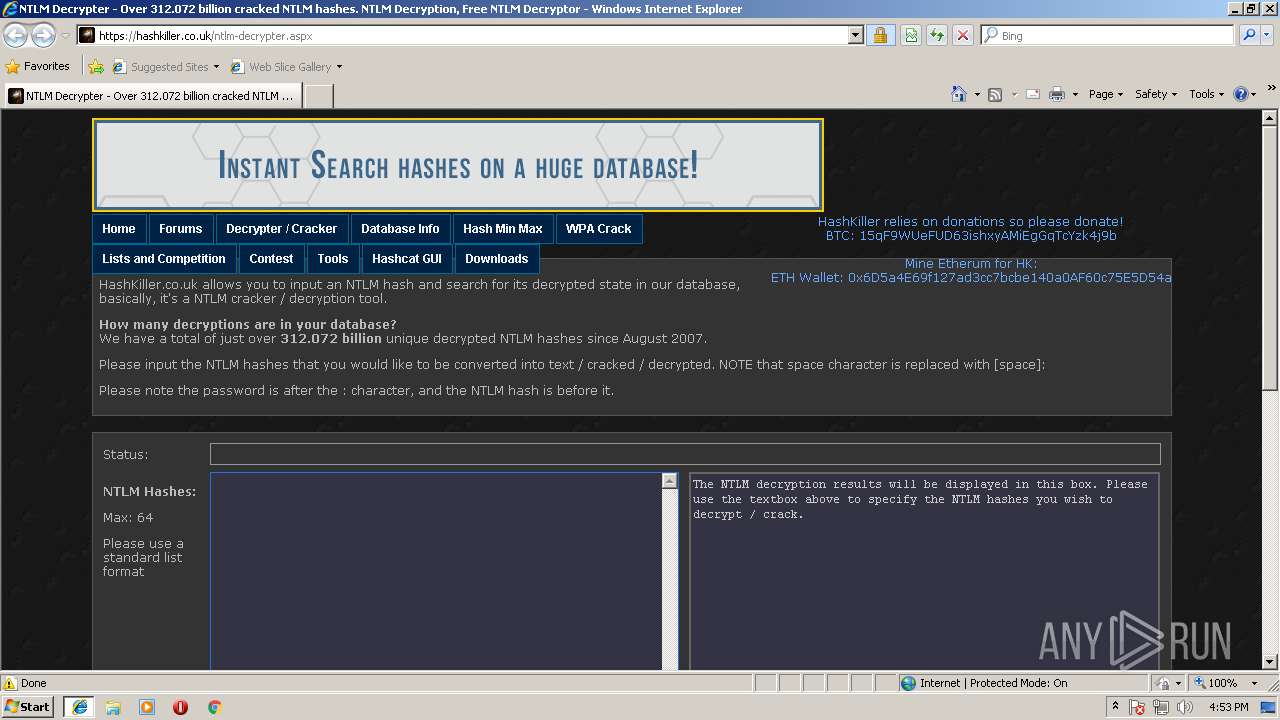
Malware analysis https://hashkiller.co.uk/ntlm-decrypter.aspx Malicious activity | ANY.RUN - Malware Sandbox Online

A novel secure and efficient hash function with extra padding against rainbow table attacks | Cluster Computing

Awesome-Password-Cracking - A Curated List Of Awesome Tools, Research, Papers And Other Projects Related To Password Cracking And Password Security

![Hashkiller - Kali Linux - An Ethical Hacker's Cookbook [Book] Hashkiller - Kali Linux - An Ethical Hacker's Cookbook [Book]](https://www.oreilly.com/api/v2/epubs/9781787121829/files/assets/714fa5ac-a3a0-4378-b325-97dee1e71141.png)


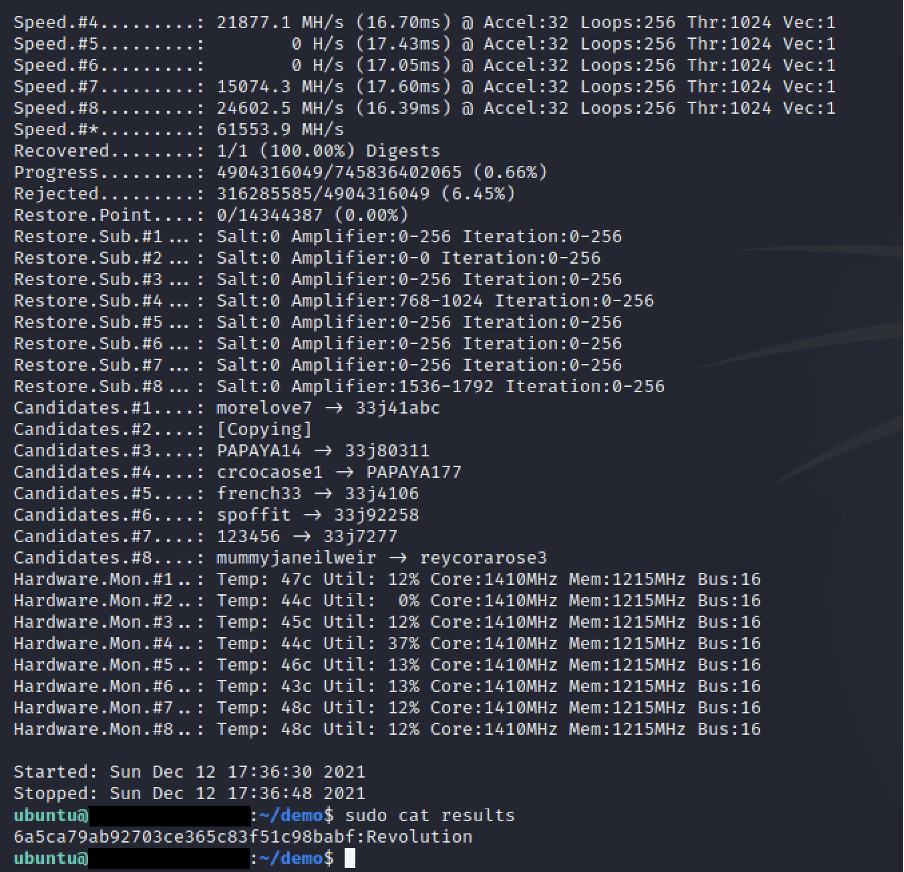








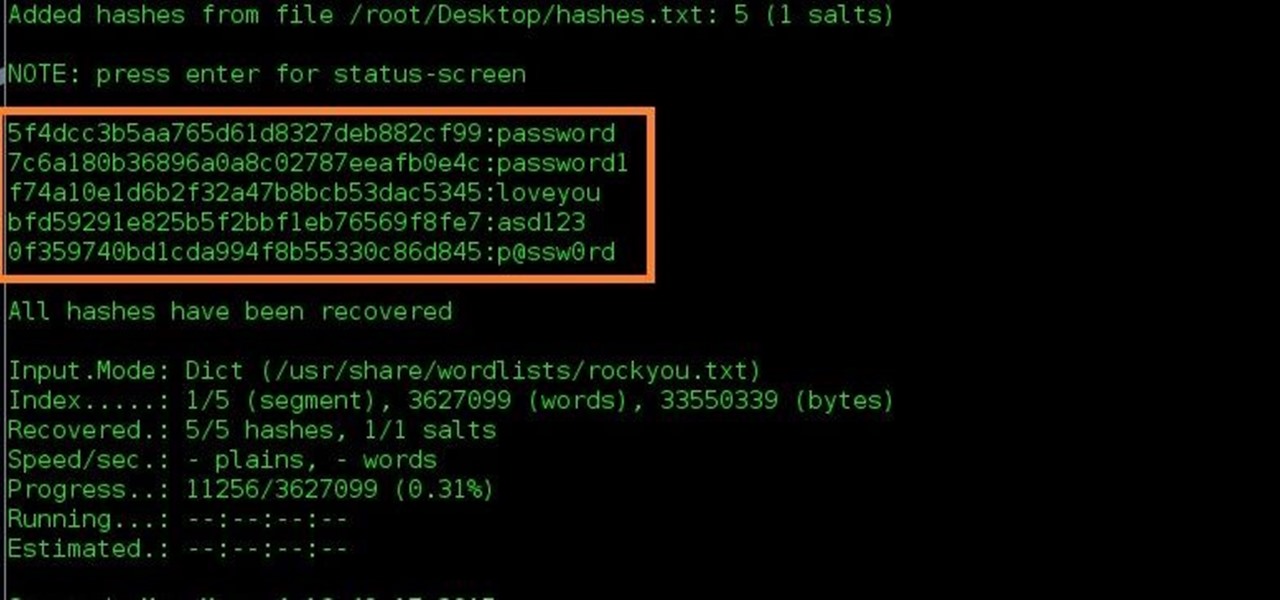


![Hashkill 0.3.1] Password Cracker Tool Released Hashkill 0.3.1] Password Cracker Tool Released](https://1.bp.blogspot.com/-O1NukABHlPk/UR5psXWGd_I/AAAAAAAAUhM/0D34wxep8qQ/s1600/Password+Cracker+Tool+Hashkill+version+0.3.1+released.png)